
Security is a primary concern for any mass IoT deployment and extremely important for any LPWAN.
LoRaWAN™
utilizes two layers of security: one for the network and one for the
application. The network security ensures authenticity of the node in
the network while the application layer of security ensures the network
operator does not have access to the end user’s application data.
Accordingly, the LoRaWAN specification defines two layers of cryptography:
- A unique 128-bit Network Session Key shared between the end-device and network server
- A unique 128-bit Application Session Key (AppSKey) shared end-to-end at the application level
Data
over LoRaWAN is encrypted twice; sensor data is encrypted by the node,
and then it is encrypted again by the LoRaWAN protocol; only then is it
sent to the LoRa Gateway. The Gateway sends data over normal IP network
to the network server.
The
Network server has the Network Session Keys (NwkSkey), and decrypts the
LoRaWAN data. It then passes the data to the Application server which
decrypts the sensor data, using the Application Session Key (AppSKey).
This
is important since LoRa Gateway operate over open frequency so can
receive data from any sensor in the vicinity. Thus, it become important
that the LoRa Gateways not have ability to decrypt sensor data.
It
is important to note that it is the LoRaWAN communication protocol that
adds the encryption. LoRa transmissions by themselves are simple radio
wave transmission and cannot be encrypted.
LoRaWAN™ devices have two ways to join the network. The first is OTAA,
Over-the-Air-Activation. The device and the network exchange a 128-bit
AppKey. When the device send the join request, the AppKey is used to
create a Message Integrity Code (MIC),
the server then check the MIC with the AppKey. If the check is valid,
the server creates two new 128-bit keys, the App Session key (AppSkey) and the Network Session Key (NwkSkey).
These keys are sent back to the device using the AppKey as an
encryption key. When the keys are received the device decrypts and
installs the two session keys.
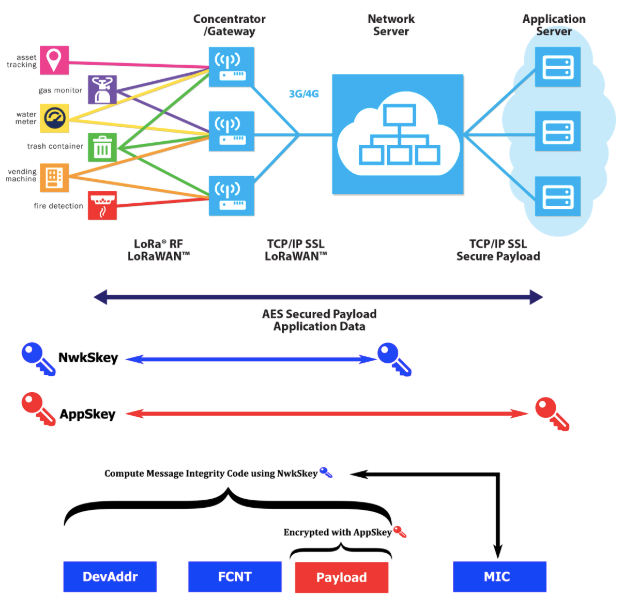
The NwkSkey is used to guarantee the message integrity from the device to the LoRa Network Server. The AppSkey is used for the end-to-end AES-128 encryption from the device to the Application Server.
The second method for the network join is ABP,
Activation by Personalization. In this case the device session keys are
inserted by the user, thus is possible to have security issues.
LPWAN - Fundamentals of IoT (Part1)
LoRa and LoRAWAN - Fundamentals of IoT (Part 2)
Source :Internet



0 comments:
Post a Comment